Triage: Group Modifications in Windows
Modifications to Groups in Windows are some of the more common incidents an analyst can face. It is important that you can correctly interpret the logs to ensure correct information is escalated.
Why do we look at group modifications?
Group modifications are one of the more obvious methods of privilege escalation in a Windows environment, we can map this to the ‘Valid Accounts’ MITRE ATT&CK Technique. (Specifically sub-techniques 002 and 004)
Modifications to Security-Enabled groups in Windows are usually monitored by a Security Operations Centre to analyse any anomalous group modifications. This could include an account performing an exploit to escalate its own privileges, or creation a new account followed by use of a previously compromised privileged account to escalate privileges of the new account to evade detection.
From an internal security standpoint, these events may also be monitored to ensure privileged users are following best practice and not elevating Dave from Accounting to Domain Administrators to install some software.
Security-Enabled & Security-Disabled
Security Enabled groups give users within them certain privileges, whilst Security Disabled groups are for distribution lists in exchange.
We won’t go into Security Disabled groups in this blog, but just keep note that they are not associated with the same risks as Security-Enabled groups and do not allow users any additional privileges.
Scope: Local, Global, Universal Groups
When looking at group mods, we need to be aware of the scope that a group has. Within Windows environments this boils down to Local, Global and Universal groups.
Local groups are ‘Local’ to the machine that the group is present on, a well-known group being Built-in Administrators, Global groups are effective across an entire domain, a well-known group being Domain Administrators. Finally, Universal groups are effective across an entire organization spanning multiple domains, a well-known group being Enterprise Administrators.
It is important to note the difference between scope and privilege, for example you could see a Global group that only gives privileges to use an end-user application across the domain, this is likely less risky than Built-in Administrators, although Built-in Administrators is local to one device users in this group have full administrative privileges on that device.
In short:
A Local group does not always mean Built-in Administrators, a Global group does not always equal Domain Administrators and a Universal Group does not always mean Enterprise Administrators.
Log Breakdown
Below is a log obtained from Windows Event Viewer, firstly, lets look at three main sections that tell us about what is happening: Subject, Member and Group.
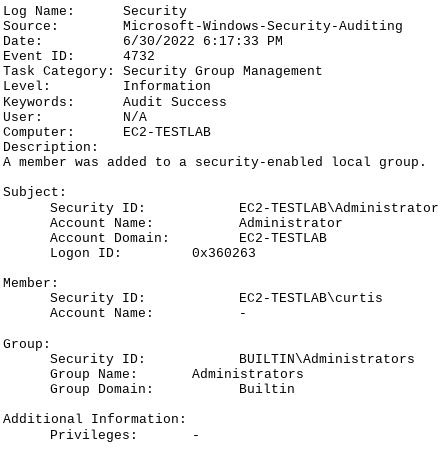
Subject - This section shows details about the user performing the operation
Member - This section shows details about the account that the operation is being performed on
Group - This lists details of the group that the account is being added to/removed from
Depending on where a log is obtained, you may see some minor changes in how the log is laid out and field names. Most notably Group is sometimes parsed into a field called 'Target User' or 'Target'.
