What the hell is that DLL? – Better Triage resources
Note to SOC Analysts:
Take a breather, it’s over.
After crawling through all the sh*te webpages with the description “How to remove from pc virus plz **FIX FREE Download*”.
You've found it.
The blog post that will actually tell you where to find out what that DLL or executable you found is, along with what it does.
What is covered in this guide?
This blog post is by no means a deep dive, however it does aim to provide a more effective way to triage incidents that avoids using standard search engines.
Scenarios:
Windows Native Process or DLL
Web traffic to legitimate sites with a weird context
Unknown file extension
Triage Resource Links:
Scenario 1 - Windows Native Process or DLL
Let’s say you are looking through some logs and encounter a DLL or .EXE that you don’t recognize.
If you have ever searched for “xxx.dll” or “xxx.exe” with a search engine, you will be treated to this:
Usually we have three questions:
What is it?
Is it bad?
What does it do?
What is it? - Strontic xCyclopedia
In the developers own words ‘The xCyclopedia project attempts to document all executable binaries (and eventually scripts) that reside on a typical operating system. Currently, this includes all observed EXE and DLL files, as well as COM Objects’
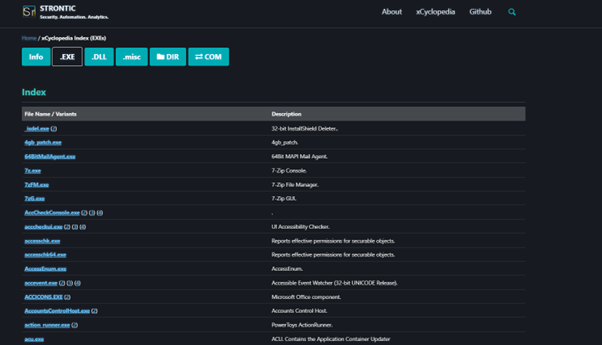
This is a great resource to identify if the executable or DLL you are looking at is commonly found or if it is anomalous.
Included is a mock folder structure which can be used to identify common configuration/install file locations.
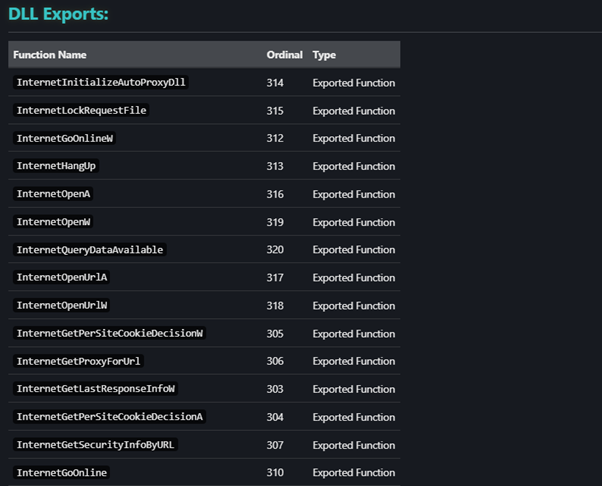
xCyclopedia is very useful when looking at DLL files as the information pages contain DLL Export functions. These functions are the key to knowing what capabilities our DLL has.
The xCyclopedia also contains COM (Component Object Model) objects which can be searched by their CLSID.
This is a bit heavy to go into here, if you are interested you can read more about COM objects here COMObjects and Interfaces - Win32 apps | Microsoft Learn
Is it bad? - LOLBAS
LOLBAS is a collection of LOLBins (Living off the land binaries); Microsoft signed processes usually present in a Windows environment which can be used for malicious purposes.
This means an attacker can perform malicious activities without having to pull in extra tools or malware, hence ‘living off the land’ they are currently residing in.
If you encounter a Windows system process in logs and you are not sure if this is being used maliciously, you can check LOLBAS to see if this is a known LOLBin, you can then see different malicious uses mapped to MITRE ATT&CK techniques.

This information contains command line examples which you can use to identify familiar patterns in logs you are investigating.
Each binary will usually come with some detections which can be useful for threat hunting or adding your own detection ruleset.
There is also a site for ‘living off the land’ in a Unix environment GTFOBins.
What does it do? – MalAPI/Windows API Documentation
MalAPI is a resource created by mrd0x (Twitter: @mrd0x) which provides information about the export functions contained in DLL files.
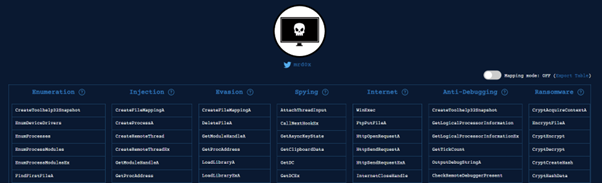
This is where it gets a bit technical, but if you see a DLL export function in xCyclopedia that also appears in this list, then its likely worth a further look to see what it does.
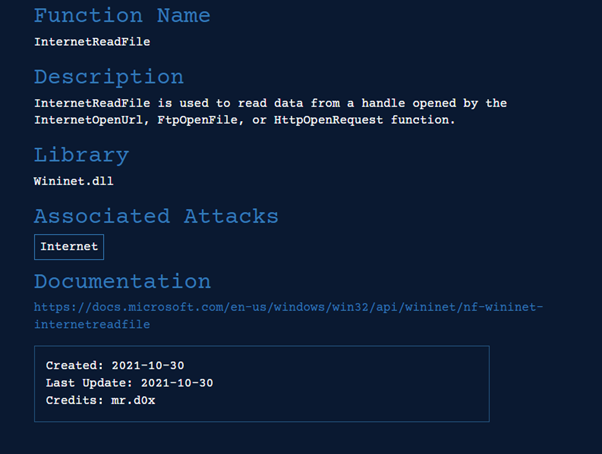
Each entry in MalAPI.io contains a link to the Microsoft Documentation.
If your function isn’t present you could try directly searching in the Microsoft Documentation WindowsAPI index - Win32 apps | Microsoft Learn
Scenario 2 – Web traffic to legitimate sites with a weird context
From time to time you may see traffic to a legitimate site, however this could be anomalous. For example, you see a device connecting to Facebook.
It is easy to dismiss this as legitimate traffic just based off the domain being known, but what if this was seen on a server instead of an end-user device?
It may seem like this traffic could only be legitimate, but an infected machine can scrape a Facebook profile for posts that contain commands.
Take your fingers off the false positive button and take a look at LOTS Project - Living Off Trusted Sites(lots-project.com). This is another resource created by mr.d0x.
This site contains a list of legitimate sites and scenarios where they can be used maliciously.
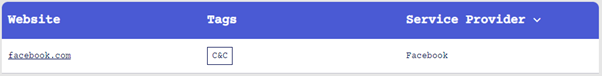
The ‘LOTS Project’ contains many examples such as this that are worth knowing about and using to inform your triage.
Attackers think outside of the box, so you need to as well.
Scenario 3 - Unknown file extension
The final tool in this list is a great targeted way to search for file extensions, another addition from mr.d0x.
Filesec.io contains information about file extensions, which binaries they are associated with and how they can be used maliciously.
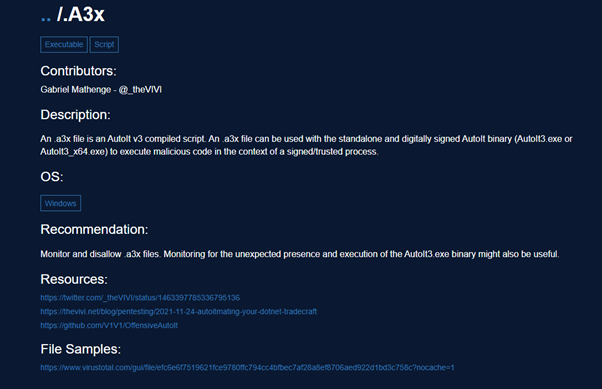
This site is more reliable than the standard search engine results which can lead to nowhere.
Summary
Hopefully this guide can help reduce a reliance on Google and save time when trying to find out what a process or DLL does.
It is worth adding all these resources to your toolkit and exploring them yourself to uncover their full functionality.
